Troubleshoot Avaya Workplace – Failed to Parse all Certificates
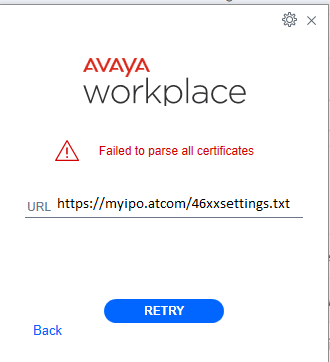
Running into problems with registering the Avaya Workplace Client for Windows? We have some troubleshooting tips for you! The following step-by-step guide will detail the actions we took to track down a cryptic error: “Failed to parse all certificates”
Step 1: Browse to the address you are trying to use to register Workplace
In our example, you would open a browser windows and enter “https://myipo.atcom/46xxsettings.txt” in the browser address bar. If the certificates you have loaded into your IP Office are valid you shouldn’t see any complaints from your browser. You can click the little sliders in Chrome (or the padlock in Edge) then “Connection is Secure” then “Certificate is Valid” to get more info. If your browser complains that the connection is not secure, you’ve got some work to do in terms of fixing your 3rd party SSL certificate!
Step 2: Acquire logs from the Avaya Workplace app
Click the gear in the upper right corner of Workplace, got to Support, then click “Report a Problem”. The Workplace software will generate internal logs then open your email client to send them. Rather than sending the email, open the ZIP attachment. There are a few useful files in there but the one that helped us is called “UccLog.log”
Step 3: Search the Log Files for your Error
Open log files in your favorite text editor (notepad, etc.) and search for your particular error message. For example, in our case we searched for “parse” since it was a key word in the error description. Our search found this line which described the actual problem:
2024-08-21 14:14:07.518 I [16676/UI] [UCCL] CertificateDownloader: Failed to load certificates from file https://myipo.atcom/2024CA.pem, error = ParsingError
Step 4: Fix the Problem!
Now that we knew 2024CA.pem was the certificate Workplace couldn’t parse, we tried browsing to the file. It didn’t exist! Turns out the file name was a reference to a previously used cert that didn’t exist anymore after an upgrade to R12. All we had to do was change a portion of 46xxspecials from this:
# GENERALSPECIALS
SET TRUSTCERTS WebRootCA.pem,2024CA.pem
SET ENABLE_PUBLIC_CA_CERTS 1
# GROUP_SETTINGS
to this:
# GENERALSPECIALS
SET TRUSTCERTS WebRootCA.pem
SET ENABLE_PUBLIC_CA_CERTS 1
# GROUP_SETTINGS
If you have any questions or comments about this topic, feel free to chime in on our Sundance Technical Forum.
Discover more from IP Office Assistance
Subscribe to get the latest posts sent to your email.