Using Lets Encrypt Certificates for Signed Certificates in
IP Office Contact Center
The purpose of this document is to provide guidelines for configuring Lets Encrypt certificates in IP Office Contact Center (IPOCC) and enable automatic updates to provide Signed Certificate validation for clients
Steps
Using Apache Tomcat as the Web Server
Using Internet Information Server as the Web Server
Installing Win-ACME service for Lets Encrypt
Creating Certificates using IIS
Creating Certificates using Apache Tomcat
Creating and Modifying the Batch file(s)
Replacing an Existing Signed Certificate
Fresh Installation of a new Certificate and Automatic Renewals
Requirements:
- DNS “A” Records need to be created in the Public DNS Server pointing to the Public Firewall that will NAT port forward to the IPOCC internal address
- DNS records need to be created in the Internal DNS Server pointing to the IPOCC Internal IP Address
- OpenSSL installed on the IPOCC Server
- Either IIS installed or a Separate instance of Apache Tomcat listening on a Non SSL port and the port must not conflict with an IPOCC default port. Example port 80, 6080, 9080
- IPOCC must be accessible on the above port through the public facing firewall.
- Win-Acme client for Lets Encrypt
- An email address of a system administrator who will receive notifications of a pending certificate expiry in the event of failed renewals.
- Your favourite Text Editor such as Notepad, Notepad++ etc
- Some knowledge working with Batch files.
Before you Begin
Do not proceed until you have understood the points below and made copies of respective files.
- This application note is written with the assumption that this is the first time a signed certificate will be installed in the Java Keystores, replacing the default Self Signed Certificate. If there is already a certificate that was previously manually installed either from Lets Encrypt or another certificate authority, please refer to the Addendum for special consideration.
- Even if currently using the default Self Signed Certificate, it is recommended that you backup (make a copy) the “tomcat.jks” file in each of the three Web Services stores. This way if an issue is encountered you can restore the self signed certificate.
- The tomcat.jks files are located at. All three have different passwords so please make a copy of all three
- C:\Program Files (x86)\Avaya\IP Office Contact Center\Tomcat\conf
- C:\Program Files (x86)\Avaya\IP Office Contact Center\Tomcat WWW\conf
- C:\Program Files (x86)\Avaya\IP Office Contact Center\Web Service Collection\conf
- By Default, every installation of IPOCC dynamically creates a password for the Java Key Store. This ensures that no two installs have the same passwords. The passwords are stored in the Server.xml file located in the same directory as the tomcat.jks file. Double Clicking the XML file will open in a Web Browser. Locate the entry “keystorePass=” You will need the passwords from each of the 3 Server.xml files when modifying the batch files.

DNS Records
DNS records (especially public DNS records) can take up to 4 hours to be replicated across DNS servers on the internet. Often this happens much quicker, however for installation purposes ensure that the DNS records are created on the Public (and Private) DNS servers ahead of time.
At minimum there should be an “A” Record created on the DNS Server pointing to the relevant IP Address of the IPOCC Server.
For a Public DNS Server, this would likely be the firewall address which would have a rule to either forward all traffic to the IPOCC, or only traffic on specific ports.
For the Internal DNS (if applicable) the A record would point to the internal IP Address of the IPOCC Server.
Depending on the capabilities of the DNS server, it may be possible to create “Redirects” in order to redirect an easy to remember name to a desired Server port to make it easier for users.
Note: The name does not have to match the Servers Name.
An example of an A record would be:
ipocc.example.com A 111.111.111.111 (see screenshot below)
An example of a redirect address (if applicable) would be:
Agent.example.com redirects to https://ipocc.example.com:28443/WebUI (see screenshot below)
DO NOT use the Stealth Option if available as it will impact how the URL is presented for certificate validation. If you intend to use Stealth Forward, you will need to ensure that your certificate includes the FQDN being used as the Forwarding name.


Web Server Installation
We will provide two options of Web Server that could be used. The choice of which one to use is personal preference. Internet Information Server (IIS) is included with Windows Server operating systems but by default not usually installed, or one can download a separate instance of Apache Tomcat.
For the sake of this document we will cover both Apache Tomcat and IIS, but only one should be installed.
IIS may be simpler when creating certificates as requires fewer steps when using the Win-ACME GUI.
Using Apache Tomcat as the Web Server
Download the latest version of Apache Tomcat from the Apache Tomcat website http://tomcat.apache.org/
At the time of this note, the latest version was R9.0 and subsequent screen shots may include the version number. Installation options may differ with different versions.




Make sure that the ports listed above are changed. By Default the IPOCC uses 3 instancec of Java Web Services so these ports cannot conflict. The HTTP Connector Port should not be either 8080, 28080.
Remember whatever port you choose you need to ensure that the port is opened on the Windows Firewall on the Server, and must be accessible remotely.
In our example we will use port 80.
The Tomcat Administration Login is optional and not required.

IMPORTANT: JRE is installed by default with IPOCC. DO NOT install Java on the Server. Use the Java Runtime that is included with IPOCC, which is part of the Java Development kit.
If you install Java on the IPOCC Server any functionality that relies on the Java Development Kit will cease working.

By default the Apache installation is to a path in Program Files. You can accept the default, or shorten the path. Shortening the path will make it easier when entering the path to the Tomcat directory during the Win-Acme configuration.



Once the Services are started make sure that you can connect to the server on the localhost to confirm the connection.
If successful check that the server can be accessed using the DNS name within remotely and confirm the same page is loaded.
If you cannot connect to the default page, either from the local server or remotely, correct the issue before continuing.
An Example of the default Web Page created by Tomcat is below.
If a webpage is created with the name index.html then Apache will display that page instead. The Index Page could be used as a landing page with some links to the actual web services page, or could be left as a blank page.

Using Internet Information Server as the Web Server
Internet Information Server (IIS) is a Windows Server Role that is not typically installed by default but can be added from the Server manager. It requires no expertise to install of configure and by default will create a Inetpub directory on the C:\ drive.
Below are some screenshots that can be expected when adding the Web Server Role to the Windows Server.





Checking the Web Server Box will automatically create a Pop up Window (next page). Select Add Features


NOTE: Adding ASP.NET is entirely optional. It is not used for any purpose on the Web Server






You should now be able to access the default website on the Server by opening your web browser and selecting http://localhost



Before updating the Server Bindings and adding your FQDN to the binding list, make sure that you can connect to the server using http://localhost in your web browser. Once you enter the binding, the server will only respond to the FQDN.
To Update the Bindings, Select the Default Website in the Left Column and then select Bindings on the Right. Edit the default binding and set the servers FQDN and port.
If you plan on changing the listening port, make sure that it does not conflict with any of the IPOCC Http ports, such as 8080 or 28080. Remember the ports will also need to be allows through the Windows Firewall on the Server as well as your Public Firewall.
Once the Binding has been updated connect to the Web Page using the Full FQDN in your web browser.
Verify that you are able to connect using a web browser on the same server, a remote PC on the LAN as well as a remote connection from an Internet connected PC.
An example of the default IIS page is below
If a webpage is created with the name index.html then Apache will display that page instead. The Index Page could be used as a landing page with some links to the actual web services page, or could be left as a blank page.

Installing OpenSSL
We will be using OpenSSL to create a PFX file from the provided certificates once issued. There are a few OpenSSL clients for Windows installs, however we used the Windows version from Shining light Productions found at https://slproweb.com/products/Win32OpenSSL.html
The version numbers are constantly changing, so select the latest version based on the time of your install. You only need the “Light” installer for your operating system. Most IPOCC installs should be using 64 bit operating systems.

Below are some screen shots that go through the installation process. Take note of the screenshot with the installation directory. The Batch file that will be used after the installation is pre-configured with this directory. If you change it here be sure to update the path in the batch file as well.



Keeping the Install path as short as possible will help with later configuration.




I am sure with more the more installs you do using this you may find the fact that the OpenSSL installer keeps the installation simple. You may want to consider making a donation to help maintain the effort.
Installing Win-ACME service for Lets Encrypt
Download the latest version of Win-Acme from the Win-ACME site on Github. Note that Win-ACME recently changed their name. You may also find references to them by the original name which was Lets Encrypt Win Simple, or just Win Simple
https://github.com/PKISharp/win-acme

The Download is a ZIP Archive.
Extract the ZIP Files to a Folder and place the folder on the root of the C:\ drive, i.e.
C:\win-acme
The contents of your Directory should look similar to the below.

Creating the Certificates
Win-ACME provides the ability to run Lets Encrypt without any command line strings to access the Lets Encrypt Production Servers, or with a Command Line String to Access the Staging Server. A Staging Server should preferably be used to test your installation and ensure that there are no issues getting your certificates validated. Once the Certificates are successfully created, run Win-Acme again without the Command line string to get your Production Certificate.
As Lets Encrypt imposes stricter rate limits as to how many times you can try and request a certificate in a day/week on the production servers vs the staging servers, therefore it is best to iron out any connectivity issues on the Staging servers.
In the Staging environment you will also have the ability to “test” the Web Page connection, which you will not get in the production environment
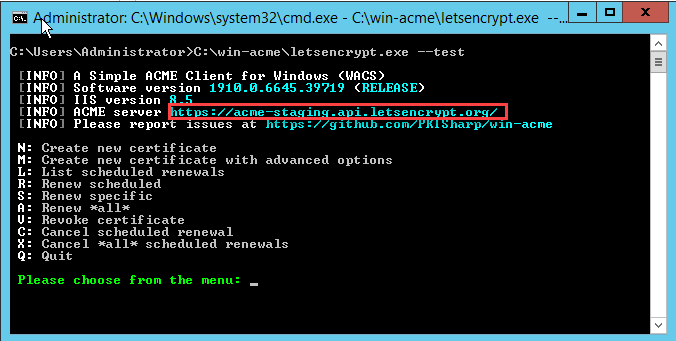
To begin using the Staging Server you should run “Lets Encrypt.exe –test”, i.e.
C:\win-acme\letsencrypt.exe –test
(See Screenshot below)
Verify that you are connected to the “acme-staging” server.

The process for generating the certificates will differ depending on whether IIS or Apache Tomcat. Refer to the relevant section based on your Web Server
Creating Certificates using IIS
When creating certificates for use on IIS, the Win-ACME client will extract the name (or names) of the Bindings web server bindings. It will also offer the ability to automatically update and enable HTTPS functionality on the IIS Server. For the sake of this example we will not enable HTTPS for the IIS site.
Below is a screenshot of the complete process. There are multiple options that can be used. While in the staging environment you can choose which works best for you.
If this is the first time that you are running the application, you will be prompted to enter in an email address where notifications of expiring certificates can be sent, as well as accept the terms of service. (Not included in the details below)
On the first question, we selected N, however M does offer more advanced options. If you only have a single site and all the Bindings are defined already in IIS then N would likely be sufficient.
For the second question regarding Bindings, while we chose option 2 in the example as we only have a single binding, option 1 would have also worked.
We only have the Default Web Site defined so could select that. If you created a new Web Site then be sure to select the correct Site, as the Bindings will be extracted automatically.
When prompted to test the connection in your web browser select Y. This will open your default web browser and connect to a Dynamically created page. If this fails, then the rest of the process will fail. Correct the issue before continuing.
While we chose not to have the certificate automatically installed into IIS, this is optional and there is no harm selecting yes.
Once completed, and the certificate was created, close the window and open it again without the Command line parameters (double click the Exe file will be sufficient).
Follow through the same process and answer the questions as in the Staging environment. At the end of the process, there are some additional prompts to add a Scheduled Task. Select Yes and use the logged on users account. If you wish to use an alternate account you can update the account settings through the task Scheduler.

Creating Certificates using Apache Tomcat
While Apache can be configured to use Host bindings we are using the basic out of the box installation
The screenshot below provides an overview of the selections needed to use Apache Tomcat when requesting the certificates
Note the Points Referenced.
For (1) you must select “M” for Advanced Options
Be sure to enter the FQDN accurately
For (2) if you installed Tomcat using it’s default installation directory, you will need to manually enter the full string to the Root directory. If you followed the suggestion provided during the installing Apache Tomcat earlier in the document, the path will be C:\Tomcat\webapps\ROOT\
Follow through the rest of the steps, remember to test the connection in your browser.
Once completed, and the certificate was created, close the window and open it again without the Command line parameters (double click the Exe file will be sufficient).
Follow through the same process and answer the questions as in the Staging environment. At the end of the process, there are some additional prompts to add a Scheduled Task. Select Yes and u se the logged on users account. If you wish to use an alternate account you can update the account settings through the task Scheduler.

Creating and Modifying the Batch file(s)
You can create this before or after generating the certificates, however after will allow you to verify the certificate name which is needed to modify the files.
There are Three Script files Embedded in this document:
- Createcert.bat.txt – Only needs to be used if the IPOCC already has a previously installed signed certificate
- Certimport.bat.txt – This is used for New Installs and Renewals
- CertviewKeystore.bat.txt – A handy script that will allow you to view the certificates.
The Embedded file can be modified and renamed to .bat by removing the “.txt” file extension. It is provided for convenience only. The script has been tested and proven to work, however no support is provided.
A full copy of each script is also provided in the Appendix Section. Simply copy and paste into a notepad file and save it as a “.bat” file.
Once modified and renamed, save the file on the root of the C:\ drive. This file will be used to create a scheduled Task once the certificate has been installed.
It is only necessary to modify the settings identified in the first section of the file. The remainder of the script refers to references in the first part of the script
All Tomcat and Keytool directories use the default installation directory used by IPOCC. Installing IPOCC in a different drive or changing the directories is not recommended or supported. If you changed your install directory then you must also update those fields.
All Lines begin with “SET” but not included here. Only modify the entries as identified below as required
If you installed OpenSSL in a different directory then correct the file path
OpenSSL=C:\OpenSSL\bin\openssl.exe
TomcatStorePass=”Replace_me_with_Tomcat_password” (Located in the Server.xml file as identified in the Before you begin section)
WebStorePass=”Replace_me_with_WebServiceCollection_password”
(Located in the Server.xml file as identified in the Before you begin section)
TomcatWWWStorePass=”Replace_me_with_TomcatWWW_password”
(Located in the Server.xml file as identified in the Before you begin section)
The Section below relates to the Lets Encrypt Certificates. The directory is the default directory used by Win-ACME to store the certificates. By Default Win-ACME uses the first FQDN when creating the certificates even if adding multiple names in a single instance. For instance, if the first name entered when creating the certificate was ipocc.example.com then your file names will typically be ipocc.example.com-<name>.xxx
When modifying the FQDN portion DO NOT remove the “-<name>.xxx”
PFXAll=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-all.pfx
FullChainPEM=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-chain.pem
PrivKey=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-key.pem
PFXCert=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-openssl.pfx
PFXPass=Replace_with_a_Strong_Password
Running the Batch File
The first time the certificate is created, the Batch file should be manually run. Once the batch file has been run, you will have the option to allow the batch file to automatically exit, or if you press Option 2, you can then scroll up and view the commands and ensure that there are no errors. If the view shows messages like File Overwrite that is fine. If the View shows errors like files that cannot be created, services that cannot be stopped / started, or exits out prematurely, then there is an issue with some of the file name modifications that need to be addressed.
Replacing an Existing Signed Certificate
As already stated, if you already have a signed certificate on the server and switching to Lets Encrypt then you Must first Manually install the Certificate file using the IPOCC Web UI and replace the existing Certificate. To create the Certificate use the “Createcert.bat” file and modify the values as identified above to first create the certificate, and then upload the certificate to the IPOCC Server using the WebUI.
See Appendix A for Script contents or review the embedded file
Fresh Installation of a new Certificate and Automatic Renewals
It is important to have the settings in this file correct. This is the file that will get called by the Task Scheduler on a daily / weekly basis to check for new certificates and then update the Server. If there are errors on first run then there will always be errors
For a Fresh installation, once the Certificate has been created and the file modified with the correct certificate names, run the Batch file and Pause the file at the end. Scroll up and ensure that there are no errors. There should be 3 indications that the File in the Keystore was overwritten. If not then there is a password issue or the file names were not correctly defined.
Creating a Scheduled Task
Once everything has been configured and the certificate is successfully installed, the last remaining task is to create a Scheduled Task.
IMPORTANT: When replacing the existing certificate, Tomcat requires the Web Services to be restarted. Make sure that the certificate is being replaced at a time / day that will have minimal impact, like late at night or on a weekend.
Follow the Steps below to create the scheduled Task.
Select Start – Run and type Taskschd.msc and Enter

Create a New Basic Task


Choose whether the script will run on a daily or weekly basis. For this example we are using Daily and repeating every day.

Choose a time that will not interfere with the users accessing the webUI when the Tomcat services restart


Browse to where the certimport.bat file is located, in this example the file is located on the root of the C:\drive



Provide an Account that has suitable privileges to run with the Highest Privileges.
Please remember that if you are planning on using the Administrator account, but have a password policy enforced for this account, then you should create an alternate account that does not have the same restrictions, or you will need to keep updating the password.

Congratulations, you should now have configured your IPOCC Server to allow the use and automatic updates of Lets Encrypt Certificates.
Appendix A
Use this for a System that already has an Existing Signed Certificate which is being replaced by Let’s Encrypt
Copy everything between the Lines.
@ECHO OFF
:REM Define Path to Keytool and OpenSSL. Keytool is installed by default with IPOCC installation.
SET keytool=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Java Development Kit\bin\keytool.exe”
SET OpenSSL=C:\OpenSSL\bin\openssl.exe
:REM Define Path to IPOCC Tomcat Directory and Password.
SET TomcatKeyStore=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Tomcat\conf\tomcat.jks”
SET TomcatStorePass=”Replace_me_with_Tomcat_password”
:REM Define Path to IPOCC Web Service Collection directory and Password
SET WebServiceKeystore=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Web Service Collection\conf\tomcat.jks”
SET WebStorePass=”Replace_me_with_WebServiceCollection_password”
:REM Define Path to IPOCC TomcatWWW directory and Password
SET TomcatWWWKeyStore=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Tomcat WWW\conf\tomcat.jks”
SET TomcatWWWStorePass=”Replace_me_with_TomcatWWW_password”
:REM Define Alias for Certificate and Keystore. Define the PFXPassword needed to import into the Keystore and Define the path and name of the Key to be imported
SET Alias=”tomcat”
SET PFXAll=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-all.pfx
SET FullChainPEM=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN.com-chain.pem
SET PrivKey=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-key.pem
SET PFXCert=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-openssl.pfx
SET PFXPass=Replace_with_a_Strong_Password
: REM DO NOT Modify any of the values below this line. If you need to add a PAUSE to check for an issue you may but do not modify the commands.
: REM If something isn’t working it is because something above is incorrect such as a wrong password, wrong file name or wrong directory
ECHO ON
:REM We will determine if the certificate has been renewed by looking for a PFX file that will be created with the renewal but we won’t need it as we will create our own using OpenSSL
IF EXIST %PFXALL% Goto :OpenSSL
goto :end
:OpenSSL
:REM Create PFX file using OpenSSL
%OpenSSL% pkcs12 -export -in %FullChainPEM% -inkey %PrivKey% -password pass:%PFXPass% -out %PFXCert% -name %Alias%
:REM To prevent this always running, we will delete the PFXALL file as we don’t need it any longer and will allow us to only update the server when a certificate is renewed
Del %PFXALL%
:end
@Echo OFF
Echo.
Echo.
Echo Please select one of the following. Default is 1
Echo.
Echo 1. Exit
Echo 2. Pause the Screen to check for Errors
Echo.
@Echo Off
CHOICE /T 10 /D 1 /C 12
if errorlevel 2 goto :Pause
if errorlevel 1 goto :Exit
:Pause
Echo.
Echo.
Echo.
Echo Pausing to check for errors.
Echo.
Echo.
PAUSE
:Exit
Exit
Stop copying above the line
Appendix B
Use this for a New System that currently does not have a Signed Certificated as well as any subsequent Automatic Renewals
Begin Copying below the line
@ECHO OFF
:REM Define Path to Keytool and OpenSSL. Keytool is installed by default with IPOCC installation.
SET keytool=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Java Development Kit\bin\keytool.exe”
SET OpenSSL=C:\OpenSSL\bin\openssl.exe
:REM Define Path to IPOCC Tomcat Directory and Password.
SET TomcatKeyStore=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Tomcat\conf\tomcat.jks”
SET TomcatStorePass=”Replace_me_with_Tomcat_password”
:REM Define Path to IPOCC Web Service Collection directory and Password
SET WebServiceKeystore=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Web Service Collection\conf\tomcat.jks”
SET WebStorePass=”Replace_me_with_WebServiceCollection_password”
:REM Define Path to IPOCC TomcatWWW directory and Password
SET TomcatWWWKeyStore=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Tomcat WWW\conf\tomcat.jks”
SET TomcatWWWStorePass=”Replace_me_with_TomcatWWW_password”
:REM Define Alias for Certificate and Keystore. Define the PFXPassword needed to import into the Keystore and Define the path and name of the Key to be imported
SET Alias=”tomcat”
SET PFXAll=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-all.pfx
SET FullChainPEM=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN.com-chain.pem
SET PrivKey=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-key.pem
SET PFXCert=C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org\Replace_my_FQDN-openssl.pfx
SET PFXPass=Replace_with_a_Strong_Password
: REM DO NOT Modify any of the values below this line. If you need to add a PAUSE to check for an issue you may but do not modify the commands.
: REM If something isn’t working it is because something above is incorrect such as a wrong password, wrong file name or wrong directory
ECHO ON
:REM We will determine if the certificate has been renewed by looking for a PFX file that will be created with the renewal but we won’t need it as we will create our own using OpenSSL
IF EXIST %PFXALL% Goto :OpenSSL
goto :end
:OpenSSL
:REM Create PFX file using OpenSSL
%OpenSSL% pkcs12 -export -in %FullChainPEM% -inkey %PrivKey% -password pass:%PFXPass% -out %PFXCert% -name %Alias%
:REM To prevent this always running, we will delete the PFXALL file as we don’t need it any longer and will allow us to only update the server when a certificate is renewed
Del %PFXALL%
:REM Importing new Certificate to Java Keystore
%keytool% -alias %Alias% -importkeystore -srckeystore %PFXCert% -srcstorepass %PFXPass% -srcalias %Alias% -srcstoretype PKCS12 -deststoretype jks -destkeystore %TomcatKeyStore% -deststorepass %TomcatStorePass% -destkeypass %TomcatStorePass% -destalias %Alias% -noprompt
%keytool% -alias %Alias% -importkeystore -srckeystore %PFXCert% -srcstorepass %PFXPass% -srcalias %Alias% -srcstoretype PKCS12 -deststoretype jks -destkeystore %WebServiceKeystore% -deststorepass %WebStorePass% -destkeypass %WebStorePass% -destalias %Alias% -noprompt
%keytool% -alias %Alias% -importkeystore -srckeystore %PFXCert% -srcstorepass %PFXPass% -srcalias %Alias% -srcstoretype PKCS12 -deststoretype jks -destkeystore %TomcatWWWKeyStore% -deststorepass %TomcatWWWStorePass% -destkeypass %TomcatWWWStorePass% -destalias %Alias% -noprompt
:REM Restart Services
:REM Stop TomcatWSC
TASKKILL /F /IM tomcat_wsc.exe
:REM Stop Tomcat
TASKKILL /F /IM tomcat.exe
:REM Stop TomcatWWW
TASKKILL /F /IM tomcat_www.exe
:StartServices
Net START “IPOCC Tomcat”
Net START “IPOCC Tomcat WSC”
Net START “IPOCC Tomcat WWW”
:end
@Echo OFF
Echo.
Echo.
Echo Please select one of the following. Default is 1
Echo.
Echo 1. Exit
Echo 2. Pause the Screen to check for Errors
Echo.
@Echo Off
CHOICE /T 10 /D 1 /C 12
if errorlevel 2 goto :Pause
if errorlevel 1 goto :Exit
:Pause
Echo.
Echo.
Echo.
Echo Pausing to check for errors.
Echo.
Echo.
PAUSE
:Exit
Exit
End Copying Above the line
Appendix C
This script can be used to view and inspect the certificates installed in each of the three Keystores
Begin copying below the line
@ECHO OFF
:REM Define Path to Keytool and OpenSSL. Keytool is installed by default with IPOCC installation.
SET keytool=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Java Development Kit\bin\keytool.exe”
:REM Define Path to IPOCC Tomcat Directory and Password.
SET TomcatKeyStore=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Tomcat\conf\tomcat.jks”
SET TomcatStorePass=”Replace_me_with_Tomcat_password”
:REM Define Path to IPOCC Web Service Collection directory and Password
SET WebServiceKeystore=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Web Service Collection\conf\tomcat.jks”
SET WebStorePass=”Replace_me_with_WebServiceCollection_password”
:REM Define Path to IPOCC TomcatWWW directory and Password
SET TomcatWWWKeyStore=”C:\Program Files (x86)\Avaya\IP Office Contact Center\Tomcat WWW\conf\tomcat.jks”
SET TomcatWWWStorePass=”Replace_me_with_TomcatWWW_password”
Echo ON
: Certificates will be printed one certificate at a time to avoid viewing multiple keystores in the same view. The screen is cleared between certificates.
Echo ***** IPOCC TOMCATWWW KEYSTORE******
%keytool% -list -v -keystore %TomcatWWWKeyStore% -storepass %TomcatWWWStorePass%
PAUSE
CLS
Echo ***** IPOCC TOMCAT KEYSTORE******
%keytool% -list -v -keystore %TomcatKeyStore% -storepass %TomcatStorePass%
PAUSE
CLS
Echo ***** IPOCC WEB SERVICE COLLECTION KEYSTORE******
%keytool% -list -v -keystore %WebServiceKeystore% -deststorepass %WebServicePass%
PAUSE
Exit
End Copying Above the line
Embedded Batch Files
Embedded Sample Index File
Rename the sample Files to Index.html. These are very basic files.
Discover more from IP Office Assistance
Subscribe to get the latest posts sent to your email.